windows activator micro365
microsoft 365 and 2010
https://drive.google.com/file/d/1RFxnrwfae_KolBKoBQc6fuxDlL_JDGuH/view?usp=drive_link
Services for all Windows, network analysis and monitoring, and hardware source issues
microsoft 365 and 2010
https://drive.google.com/file/d/1RFxnrwfae_KolBKoBQc6fuxDlL_JDGuH/view?usp=drive_link
In this article, we will learn about
SAM. We will learn about the passwords and how they are stored in the
SAM. We will also focus on the NTLM Authentication. At last, we will be
using a bunch of different tools to extract those credentials from SAM.
SAM is short for the Security Account
Manager which manages all the user accounts and their passwords. It acts
as a database. All the passwords are hashed and then stored SAM. It is
the responsibility of LSA (Local Security Authority) to verify user
login by matching the passwords with the database maintained in SAM. SAM
starts running in the background as soon as the Windows boots up. SAM
is found in C:\Windows\System32\config and passwords
that are hashed and saved in SAM can found in the registry, just open
the Registry Editor and navigate yourself to HKEY_LOCAL_MACHINE\SAM.
To know how passwords are saved in windows, we will first need to understand what are LM, NTLM v1 & v2, Kerberos.
LAN Manager (LM) authentication was developed by IBM for Microsoft’s Windows Operating Systems. The security it provides is considered hackable today. It converts your password into a hash by breaking it into two chunks of seven characters each. And then further encrypting each chunk. It is not case sensitive either, which is a huge drawback. This method coverts the whole password string into uppercase, so when the attacker is applying any attack like brute force or dictionary; they can altogether avoid the possibility of lowercase. The key it is using to encrypt is 56-bit DES which now can be easily cracked.
NTLM authentication was developed to secure the systems as LM proved to be insecure at the time. NTLM’s base is a challenge-response mechanism. It uses three components – nonce (challenge), response and authentication.
When any password is stored in Windows, NTLM starts working by encrypting the password and storing the hash of the said password while it disposes of the actual password. And it further sends the username to the server, then the server creates a 16-byte random numeric string, namely nonce and sends it to the client. Now, the client will encrypt the nonce using the hash string of the password and send the result back to the server. This process is called a response. These three components (nonce, username, and response) will be sent to Domain Controller. The Domain Controller will recover the password using hash from the Security Account Manager (SAM) database. Furthermore, the domain controller will check the nonce and response in case they match, Authentication turns out to be successful.
Working of NTLM v1 and NTML v2 is the same, although there are few differences such as NTML v1 is MD4 and v2 is MD5 and in v1 C/R Length is 56 bits + 56-bit +16 bit while v2 uses 128 bits. When it comes to C/R Algorithm v1 uses DES (ECB mode) and v2 is HMAC_MD5. and lastly, in v1 C/R Value Length 64 bit + 64 bit + 64 bit and v2 uses 128 bits.
Now as we have understood these hashing systems, let’s focus on how to dump them. The methods we will focus on are best suited for both internal and external pen-testing. Let’s begin!
NOTE: Microsoft changed the algorithm on Windows 10 v1607 which replaced the RC4 cipher with AES. This change made all the extraction tools that directly access SAM to dump hashes obsolete. Some of the tools have been updated and handle the new encryption method properly. But others were not able to keep up. This doesn’t mean that they cannot be used anymore. This just means that if we face the latest Windows 10, we rather use update tools. Hence we divided this article into 2 parts. Windows 7 and Windows 10.
This tool is developed by Tarasco and you can download it from here. This tool extracts the SAM file from the system and dumps its credentials. To execute this tool just run the following command in command prompt after downloading:
PwDump7.exe

And as a result, it will dump all the hashes stored in SAM file as shown in the image above.
Now, we will save the registry values of the SAM file and system file in a file in the system by using the following commands:
reg save hklm\sam c:\sam reg save hklm\system c:\system

We saved the values with the above command to retrieve the data from the SAM file.
Once you have retrieved the data from SAM, you can use SamDump2 tool to dump its hashes with the following command:
samdump2 system sam

Download Invoke-Powerdump Script
The method of Metasploit involves PowerShell. After getting the meterpreter session, access windows PowerShell by using the command load PowerShell. And then use the following set of commands to run the Invoke-PowerDump.ps1 script.
powershell_import /root/powershell/Invoke-PowerDump.ps1 powershell_execute Invoke-PowerDump

Once the above commands execute the script, you will have the dumped passwords just as in the image above.
Download Get-PassHashes Script
Again, via meterpreter, access the windows PowerShell using the command load PowerShell. And just like in the previous method, use the following commands to execute the scripts to retrieve the passwords.
powershell_import /root/powershell/Get-PassHashes.ps1 powershell_execute Get-PassHashes

And VOILA! All the passwords have been retrieved.
Download Invoke-Powerdump Script
This method is an excellent one for local testing, AKA internal testing. To use this method, simply type the following in the Powershell:
Import-Module <'path of the powerdump script'>- Invoke-PowerDump

And, it will dump all the credentials for you.
NOTE: These were the tools that will only work on Windows 7. Now let’s take a look at the tools that work on Windows 10. The tools that work on Windows 10 can also work on Windows 7 but not vice-versa. The tools mentioned above work only on Windows 7. Even if they run on Windows 10 and give the hash, that hash will not be accurate and will not work and/or crack.
There is a good enough method to dump the hashes of SAM file using mimikatz. The method is pretty easy and best suited for internal penetration testing. In one of our previous article, we have covered mimikatz, read that article click here. So in this method, we will use token::elevate command. This command is responsible for allowing mimikatz to access the SAM file in order to dump hashes. Now, to use this method use the following set of commands:
privilege::debug token::elevate lsadump::sam

Impacket tool can also extract all the hashes for you from the SAM file with the following command:
./secretsdump.py -sam /root/Desktop/sam -system /root/Desktop/system LOCAL

When you have a meterpreter session of a target, just run hashdump command and it will dump all the hashes from SAM file of the target system. The same is shown in the image below:

Another way to dump hashes through hashdump module is through a post exploit that Metasploit offers. To use the said exploit, use the following set of commands:
use post/windows/gather/hashdump set session 1 exploit

Another way to dump credentials by using Metasploit is via another in-built post exploit. To use this exploit, simply background your session and run the following command:
use post/windows/gather/credential/credential_collector set session 1 exploit

The next method that Metasploit offers are by firing up the mimikatz module. To load mimikatz, use the load kiwi command and then use the following command to dump the whole SAM file using mimikatz.
lsa_dump_sam

Hence, you have your passwords as you can see in the image above.
Once you have the session by Koadic C2, use the hashdump_sam module to get passwords as shown below:
use hashdump_sam execute

All the hashes from the SAM file will be dumped as shown in the above image.
Once you have the session through the empire, interact with the session and use the mimikatz/sam module to dump the credentials with help of following commands:
usemodule credentials/mimikatz/sam execute

This exploit will run mimikatz and will get you all the passwords you desire by dumping SAM file.
LaZage is an amazing tool for dumping all kinds of passwords. We have dedicatedly covered LaZagne in our previous article. To visit the said article, click here. Now, to dump SAM hashes with LaZagne, just use the following command:
lazagne.exe all

Yay!!! All the credentials have been dumped.
CrackMapExec is a really sleek tool that can be installed with a simple apt install and it runs very swiftly. Using CrackMapExec we can dump the hashes in the SAM very quicly and easily. It requires a bunch of things.
Requirements:
Username: Administrator
Password: Ignite@987
IP Address: 192.168.1.105
Syntax: crackmapexec smb [IP Address] -u ‘[Username]’ -p ‘[Password]’ –sam
crackmapexec smb 192.168.1.105 -u 'Administrator' -p 'Ignite@987' --sam

Read More: Lateral Moment on Active Directory: CrackMapExec
John The Ripper is an amazing hash cracking tool. We have dedicated two articles on this tool. To learn more about John The Ripper, click here – part 1, part 2. Once you have dumped all the hashes from SAM file by using any of method given above, then you just need John The Ripper tool to crack the hashes by using the following command:
john –format=NT hash –show

And as you can see, it will reveal the password by cracking the given hash.
The article focuses on dumping credentials from the windows SAM file. Various methods have been shown using multiple platforms to successfully dump the credentials. To secure yourself you first must learn how a vulnerability can be exploited and to what extent. Therefore, such knowing such methods and what they can do is important.
A link refers to the connectivity between two devices. It includes the type of cables and protocols used for one device to be able to communicate with the other.
There are 7 OSI layers: 1) Physical Layer, 2) Data Link Layer, 3) Network Layer, 4) Transport Layer, 5) Session Layer, 6) Presentation Layer, and 7) Application Layer.

LAN stands for Local Area Network. It refers to the connection between computers and other network devices that are located within a small physical location.
A node refers to a point or joint where a connection takes place. It can be a computer or device that is part of a network. Two or more nodes are needed to form a network connection.

Routers can connect two or more network segments. These are intelligent network devices that store information in its routing tables, such as paths, hops, and bottlenecks. With this info, they can determine the best path for data transfer. Routers operate at the OSI Network Layer.
It refers to a direct connection between two computers on a network. A point to point connection does not need any other network devices other than connecting a cable to the NIC cards of both computers.
Anonymous FTP is a way of granting user access to files in public servers. Users that are allowed access to data in these servers do not need to identify themselves, but instead, log in as an anonymous guest.
A subnet mask is combined with an IP address to identify two parts: the extended network address and the host address. Like an IP address, a subnet mask is made up of 32 bits.
A single segment of UTP cable has an allowable length of 90 to 100 meters. This limitation can be overcome by using repeaters and switches.
Data encapsulation is the process of breaking down information into smaller, manageable chunks before it is transmitted across the network. In this process that the source and destination addresses are attached to the headers, along with parity checks.
VPN means Virtual Private Network, a technology that allows a secure tunnel to be created across a network such as the Internet. For example, VPNs allow you to establish a secure dial-up connection to a remote server.
NAT is Network Address Translation. This is a protocol that provides a way for multiple computers on a common network to share a single connection to the Internet.
The Network layer is responsible for data routing, packet switching, and control of network congestion. Routers operate under this layer.
Network topology dictates what media you must use to interconnect devices. It also serves as a basis on what materials, connectors, and terminations that is applicable for the setup.
RIP, short for Routing Information Protocol is used by routers to send data from one network to another. It efficiently manages routing data by broadcasting its routing table to all other routers within the network. It determines the network distance in units of hops.
There are several ways to do this. Install a reliable and updated anti-virus program on all computers. Make sure firewalls are setup and configured correctly. User authentication will also help a lot. All these combined would make a highly secured network.
NIC is short for Network Interface Card. This is a peripheral card that is attached to a PC in order to connect to a network. Every NIC has its own MAC address that identifies the PC on the network.

WAN stands for Wide Area Network. It is an interconnection of computers and devices that are geographically dispersed. It connects networks that are located in different regions and countries.
The physical layer does the conversion from data bits to the electrical signal, and vice versa. This is where network devices and cable types are considered and setup.
There are four layers: 1) The Network Layer, 2) Internet Layer, 3) Transport Layer, and 4) Application Layer.

Proxy servers primarily prevent external users who are identifying the IP addresses of an internal network. Without knowledge of the correct IP address, even the physical location of the network cannot be identified. Proxy servers can make a network virtually invisible to external users.
This layer provides the protocols and means for two devices on the network to communicate with each other by holding a session. This includes setting up the session, managing information exchange during the session, and tear-down process upon termination of the session.
A fault tolerance system ensures continuous data availability. This is done by eliminating a single point of failure.
The 10 refers to the data transfer rate. In this case, it is 10Mbps. The word Base refers to baseband, as opposed to broadband.
Private IP addresses are assigned for use on intranets. These addresses are used for internal networks and are not routable on external public networks. These ensure that no conflicts are present among internal networks. At the same time, the same range of private IP addresses is reusable for multiple intranets since they do not “see” each other.
NOS, or Network Operating System, is specialized software. The main task of this software is to provide network connectivity to a computer in order to communicate with other computers and connected devices.
DoS, or Denial-of-Service attack, is an attempt to prevent users from being able to access the Internet or any other network services. Such attacks may come in different forms and are done by a group of perpetrators. One common method of doing this is to overload the system server so it cannot anymore process legitimate traffic and will be forced to reset.
OSI (Open Systems Interconnect) serves as a reference model for data communication. It is made up of 7 layers, with each layer defining a particular aspect of how network devices connect and communicate with one another. One layer may deal with the physical media used, while another layer dictates how data is transmitted across the network.
The primary purpose of this is to prevent crosstalk. Crosstalk’s are electromagnetic interferences or noise that can affect data being transmitted across cables.
By using address translation instead of routing, address sharing provides an inherent security benefit. That’s because host PCs on the Internet can only see the public IP address of the external interface on the computer. Instead, it provides address translation and not the private IP addresses on the internal network.
MAC, or Media Access Control, uniquely identifies a device on the network. It is also known as a physical address or an Ethernet address. A MAC address is made up of 6-byte parts.
The TCP/IP Application layer has three counterparts on the OSI model: 1) Session Layer, 2) Presentation Layer, and 3) Application Layer.
By looking at the first octet of any given IP address, you can identify whether it’s Class A, B, or C. If the first octet begins with a 0 bit, that address is Class A. If it begins with bits 10 then that address is a Class B address. If it begins with 110, then it’s a Class C network.
OSPF, or Open Shortest Path First, is a link-state routing protocol that uses routing tables to determine the best possible path for data exchange.
Firewalls serve to protect an internal network from external attacks. These external threats can be hackers who want to steal data or computer viruses that can wipe out data in an instant. It also prevents other users from external networks from gaining access to the private network.
Star topology consists of a central hub that connects to nodes. This is one of the easiest to set up and maintain.

Advantages:
Here are pros/benefits of start topology:
Disadvantages:
Here are cons/drawbacks of using Star:
Gateways provide connectivity between two or more network segments. It is usually a computer that runs the gateway software and provides translation services. This translation is key in allowing different systems to communicate on the network.
One major disadvantage of star topology is that once the central Hub or switch gets damaged, the entire network becomes unusable.
SLIP, or Serial Line Interface Protocol, is an old protocol developed during the early UNIX days. This is one of the protocols that are used for remote access.
10.0.0.0 with a subnet mask of 255.0.0.0172.16.0.0 with subnet mask of 255.240.0.0192.168.0.0 with subnet mask of 255.255.0.0
Tracert is a Windows utility program that can use to trace the route taken by data from the router to the destination network. It also shows the number of hops taken during the entire transmission route.
A network administrator has many responsibilities that can be summarized into 3 key functions: installation of a network, a configuration of network settings, and maintenance/troubleshooting of networks.
Accessing the resources that are shared by one of the workstations on the network takes a performance hit.
A hybrid network is a network setup that makes use of both client-server and peer-to-peer architecture.
DHCP is short for Dynamic Host Configuration Protocol. Its main task is to assign an IP address to devices across the network automatically. It first checks for the next available address not yet taken by any device, then assigns this to a network device.
The main task of the ARP or Address Resolution Protocol is to map a known IP address to a MAC layer address.
TCP/IP is short for Transmission Control Protocol / Internet Protocol. This is a set of protocol layers that is designed to make data exchange possible on different types of computer networks, also known as a heterogeneous network.
Routers have a built-in console that lets you configure different settings, like security and data logging. You can assign restrictions to computers, such as what resources it is allowed access or what particular time of the day, they can browse the Internet. You can even put restrictions on what websites are not viewable across the entire network.
Use FTP (File Transfer Protocol) for file transfers between such different servers. This is possible because FTP is platform-independent.
Default gateways provide means for the local networks to connect to the external network. The default gateway for connecting to the external network is usually the address of the external router port.
Good passwords are made up of not just letters, but by combining letters and numbers. A password that combines uppercase and lowercase letters is favorable than one that uses all upper case or all lower-case letters. Passwords must be not words that can easily be guessed by hackers, such as dates, names, favorites, etc. Longer passwords are also better than short ones.
The proper termination for unshielded twisted pair network cable is 100 ohms.
Netstat is a command-line utility program. It provides useful information about the current TCP/IP settings of a connection.
For a Class C network, the number of usable Network ID bits is 21. The number of possible network IDs is 2 raised to 21 or 2,097,152. The number of host IDs per network ID is 2 raised to 8 minus 2, or 254.
Cables that are too long would result in signal loss. It means that data transmission and reception would be affected because the signal degrades over length.
Software related problems can be any or a combination of the following:
ICMP is an Internet Control Message Protocol. It provides messaging and communication for protocols within the TCP/IP stack. This is also the protocol that manages error messages that are used by network tools such as PING.
Ping is a utility program that allows you to check connectivity between network devices on the network. You can ping a device by using its IP address or device name, such as a computer name.

Peer to peer (P2P) are networks that do not rely on a server. All PCs on this network act as individual workstations.
DNS is the Domain Name System. The main function of this network service is to provide host names to TCP/IP address resolution.
One major advantage of fiber optics is that it is less susceptible to electrical interference. It also supports higher bandwidth, meaning more data can be transmitted and received. Signal degrading is also very minimal over long distances.
Here is the major difference between Hub and switch:
| Hub | Switch |
|---|---|
| A hub operates on the physical layer. | A switch operates on the data link layer. |
| Hubs perform frame flooding that can be unicast, multicast, or broadcast. | It performs broadcast, then the unicast and multicast as needed. |
| Just a singular domain of collision is present in a hub. | Varied ports have separate collision domains. |
| The transmission mode is Half-duplex | The transmission mode is Full duplex |
| Hubs operate as a Layer 1 device per the OSI model. | Network switches help you to operate at Layer 2 of the OSI model. |
| To connect a network of personal computers should be joined through a central hub. | Allow connecting multiple devices and ports. |
| Uses electrical signal orbits | Uses frame & packet |
| Does not offer Spanning-Tree | Multiple Spanning-Tree is possible |
| Collisions occur mostly in setups using hubs. | No collisions occur in a full-duplex switch. |
| Hub is a passive device | A switch is an active device |
| A network hub can’t store MAC addresses. | Switches use CAM (Content Accessible Memory) that can be accessed by ASIC (Application Specific Integrated Chips). |
| Not an intelligent device | Intelligent device |
| Its speed is up to 10 Mbps | 10/100 Mbps, 1 Gbps, 10 Gbps |
| Does not use software | Has software for administration |
There are three main network protocols supported: NetBEUI, TCP/IP, and IPX.
For Class A, there are 126 possible networks and 16,777,214 hosts. For Class B, there are 16,384 possible networks and 65,534 hosts. For Class C, there are 2,097,152 possible networks and 254 hosts
Orange/white, orange, green/white, blue, blue/white, green, brown/white, brown.
The following are the protocols under the TCP/IP Application layer: FTP, TFTP, Telnet, and SMTP.
Yes, you can connect two computers, using only one cable. A crossover type cable can be used in this scenario. In this setup, the data transmit pin of one cable is connected to the data receive pin of the other cable, and vice versa.
Ipconfig is a utility program that is commonly used to identify the addresses information of a computer on a network. It can show the physical address as well as the IP address.
A straight-through cable is used to connect computers to a switch, hub, or router. A crossover cable is used to connect two similar devices, such as a PC to PC or Hub, to the Hub.
Client/server is a type of network wherein one or more computers act as servers. Servers provide a centralized repository of resources such as printers and files. Clients refer to a workstation that accesses the server.
Networking refers to the interconnection between computers and peripherals for data communication. Networking can be done using wired cabling or through a wireless link.
Yes, that’s because MAC addresses are hard-wired into the NIC circuitry, not the PC. This also means that a PC can have a different MAC address when another one replaced the NIC card.
Clustering support refers to the ability of a network operating system to connect multiple servers in a fault-tolerant group. The main purpose of this is the if one server fails, all processing will continue with the next server in the cluster.
An anti-virus program must be installed on all servers and workstations to ensure protection. That’s because individual users can access any workstation and introduce a computer virus. You can plug in their removable hard drives or flash drives.
.
Ethernet is one of the popular networking technologies used these days. It was developed during the early 1970s and is based on specifications, as stated in the IEEE. Ethernet is used in local area networks.
In case one workstation on the network suffers a malfunction, it can bring down the entire network. Another drawback is that when there are adjustments and reconfigurations needed to be performed on a particular network, the entire network must be temporarily brought down.
CSMA/CD, or Collision Detect, retransmits data frames whenever a collision occurred. CSMA/CA, or Collision Avoidance, will first broadcast intent to send prior to data transmission.
SMTP is short for Simple Mail Transfer Protocol. This protocol deals with all internal mail and provides the necessary mail delivery services on the TCP/IP protocol stack.
Multicast routing is a targeted form of broadcasting that sends a message to a selected group of the user instead of sending it to all users on a subnet.
Encryption is the process of translating information into a code that is unreadable by the user. It is then translated back or decrypted back to its normal readable format using a secret key or password. Encryption ensures that information that is intercepted halfway would remain unreadable because the user must have the correct password or key for it.
IP addresses are displayed as a series of four decimal numbers that are separated by period or dots. Another term for this arrangement is the dotted-decimal format. An example is 192.168.101.2
Authentication is the process of verifying a user’s credentials before he can log into the network. It is normally performed using a username and password. This provides a secure means of limiting access from unwanted intruders on the network.
This is a mode of data exchange wherein two communicating computers do not use IPsec themselves. Instead, the gateway that is connecting their LANs to the transit network creates a virtual tunnel. So, it uses the IPsec protocol to secure all communication that passes through it.
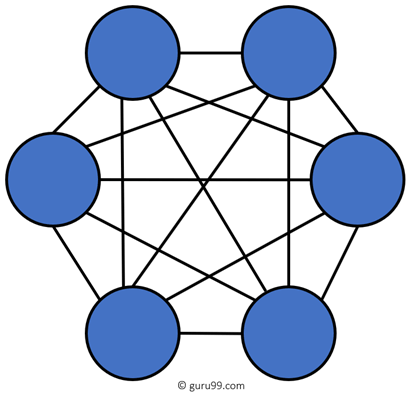
The mesh topology has a unique network design in which each computer on the network connects to every other. It is developing a P2P (point-to-point) connection between all the devices of the network. It offers a high level of redundancy, so even if one network cable fails, data still has an alternative path to reach its destination.
Types of Mesh Topology:
Partial Mesh Topology: In this type of topology, most of the devices are connected almost similarly as full topology. The only difference is that few devices are connected with just two or three devices.

Full Mesh Topology: In this topology, every node or device are directly connected with each other.
A large percentage of a network is made up of hardware. Problems in these areas can range from malfunctioning hard drives, broken NICs, and even hardware startups. Incorrect hardware configuration is also one of those culprits to look into.
A common way of dealing with such a problem is to use repeaters and hubs because it will help regenerate the signal and therefore prevent signal loss. Checking if cables are properly terminated is also a must.
Instead of having to visit each client computer to configure a static IP address, the network administrator can apply dynamic host configuration protocol to create a pool of IP addresses known as scopes that can be dynamically assigned to clients.
Profiles are the configuration settings made for each user. A profile may be created that puts a user in a group, for example.
Sneakernet is believed to be the earliest form of networking wherein data is physically transported using removable media, such as disk, tapes.
IEEE, or the Institute of Electrical and Electronics Engineers, is an organization composed of engineers that issues and manages standards for electrical and electronic devices. This includes networking devices, network interfaces, cablings, and connectors.
There are 4 protocols that are being managed by this layer. These are ICMP, IGMP, IP, and ARP.
Rights refer to the authorized permission to perform specific actions on the network. Each user on the network can be assigned individual rights, depending on what must be allowed for that user.
A VLAN is required because at the switch level. There is only one broadcast domain. It means whenever a new user is connected to switch. This information is spread throughout the network. VLAN on switch helps to create a separate broadcast domain at the switch level. It is used for security purposes.
IPv6, or Internet Protocol version 6, was developed to replace IPv4. At present, IPv4 is being used to control internet traffic but is expected to get saturated in the near future. IPv6 was designed to overcome this limitation.
RSA is short for the Rivest-Shamir-Adleman algorithm. It is the most commonly used public-key encryption algorithm in use today.
Mesh topology is a setup wherein each device is connected directly to every other device on the network. Consequently, it requires that each device has at least two network connections.
The maximum allowable length for a network segment using 100Base-FX is 412 meters. The maximum length for the entire network is 5 kilometers.
The 5-4-3 rule is used in 10Base2 and 10Base5 Ethernet architectures. In this rule, there can be a maximum of five segments in a network connected with four repeaters. Out of these five segments, only three segments can be populated with nodes.
| TCP | UDP | ||
|---|---|---|---|
| It is a connection-oriented protocol. | It is a connectionless protocol. | ||
| TCP reads data as streams of bytes, and the message is transmitted to segment boundaries. | UDP messages contain packets that were sent one by one. It also checks for integrity at the arrival time. | ||
| TCP messages make their way across the Internet from one computer to another. | It is not connection-based, so one program can send lots of packets to another. | ||
| TCP rearranges data packets in the specific order. | UDP protocol has no fixed order because all packets are independent of each other. | ||
| The speed for TCP is slower. | UDP is faster as error recovery is not attempted. | ||
| Header size is 20 bytes | The header size is 8 bytes. | ||
| TCP is heavy-weight. TCP needs three packets to set up a socket connection before any user data can be sent. | UDP is lightweight. There are no tracking connections, ordering of messages, etc. | ||
| TCP does error checking and also makes error recovery. | UDP performs error checking, but it discards erroneous packets. | ||
| Acknowledgment segments | No Acknowledgment segments | ||
| Using handshake protocol like SYN, SYN-ACK, ACK | No handshake (so connectionless protocol) | ||
| TCP is reliable as it guarantees delivery of data to the destination router. | The delivery of data to the destination can’t be guaranteed in UDP. | ||
| TCP offers extensive error checking mechanisms because it provides flow control and acknowledgment of data. | UDP has just a single error checking mechanism that is used for checksums. |
Here, are three most important elements of the protocol:
The maximum length for a network segment using 100Base-FX is 412 meters.
The decoder is a type of circuit that converts the encoded data to its original format. It also converts the digital signal into an analog signal.
Brouter is also known as Bridge Router. It is a device that acts as both a bridge and a router. As a bridge can forwards data between the networks. It also routes the data to specified systems within a network.
By using a Virtual Private Network (VPN), users can connect to the organization’s network. Corporate companies, educational institutions, government offices.
The OSI model was started in February 1980. In 802.XX, ’80’ stands for the year 1980, and ‘2’ represents the month of February.
NVT is a set of pre-defined rules to very simple virtual terminal interaction. This terminal helps you to start a Telnet session.
The source route is a sequence of IP addresses that helps you to identify the route a datagram. You can include the source route in the IP datagram header.
Pipelining describes the sequencing of processes. When any new task begins before an ongoing task is finished, it is called sequencing.
The transmission speed of Ethernet is mostly measured in Mbps.
The length of the Thinnet cable is 185 meters.
Thicknet cable is also called as the RG8 cable.
No, Nowadays, coaxial cable no longer used in a computer network.
Most of the telephone cable uses the RJ11 connector.
It is a host that has multiple network interfaces that multiple IP addresses is called a Multi-homed Host.
The full form of EGP is Exterior Gateway Protocol. It is the protocol of the routers. It is the neighboring autonomous systems that help you to identify the set of networks that you will able to reach within or via each independent system.
When a computer in the network listen and receive the signal, they are called passive topology.
It is a false terminal which allows you external machines to connect through Telnet or log in. Without this, no connection can take place.
Redirector is a kind of software which intercepts file or prints I/O requests and translates them into network requests. This component comes under the presentation layer.
THREE-WAY handshake or a TCP 3-way handshake is a process that is used in a TCP/IP network to make a connection between the server and client. It is a three-step process that requires both the client and server to exchange synchronization and acknowledgment packets before the real data communication process starts.
Hamming code is a liner code that is useful for error detection up to two immediate bit errors. It is capable of single-bit errors.
In Hamming code, the source encodes the message by adding redundant bits in the message. These redundant bits are mostly inserted and generated at certain positions in the message to accomplish the error detection and correction process.
Here are some common applications of using Hemming code:
Here, are important benefits of Hamming code
MAC address is a unique identifier that is assigned to a NIC (Network Interface Controller/ Card). It consists of a 48 bit or 64-bit address, which is associated with the network adapter. MAC address can be in hexadecimal format. The full form of MAC address is Media Access Control address.
Here are the important reasons for using MAC address:
Here are the important types of MAC addresses:
Here, are some difference between MAC and IP address:
| MAC | IP address |
|---|---|
| The MAC address stands for Media Access Control Address. | IP address stands for Internet Protocol Address. |
| It consists of a 48-bit address. | It consists of a 32-bit address. |
| MAC address works at the link layer of the OSI model. | IP address works at the network layer of OSI model. |
| It is referred to as a physical address. | It is referred to as a logical address. |
| You can retrieve the MAC address of any device using ARP protocol. | You can retrieve the MAC address of any device RARP protocol. |
| Classes are not used in MAC address. | In IP, IPv4 uses A, B, C, D, and E classes. |
Analog signal is a continuous signal in which one time-varying quantity represents another time-based variable. These kind of signals works with physical values and natural phenomena such as earthquake, frequency, volcano, speed of wind, weight, lighting, etc.
A digital signal is a signal that is used to represent data as a sequence of separate values at any point in time. It can only take on one of a fixed number of values. This type of signal represents a real number within a constant range of values.
Here are the main differences between Analog and Digital Signal:
| Analog | Digital |
|---|---|
| An analog signal is a continuous signal that represents physical measurements. | Digital signals are time separated signals which are generated using digital modulation. |
| It is denoted by sine waves | It is denoted by square waves. |
| It uses a continuous range of values that help you to represent information. | The Digital signal uses discrete 0 and 1 to represent information. |
| The analog signal bandwidth is low | The digital signal bandwidth is high. |
| Analog hardware never offers flexible implementation. | Digital hardware offers flexibility in implementation. |
| It is suited for audio and video transmission. | It is suited for Computing and digital electronics. |
| The Analog signal doesn’t offer any fixed range. | Digital signal has a finite number, i.e., 0 and 1. |

A Metropolitan Area Network or MAN is consisting of a computer network across an entire city, college campus, or a small region. This type of network is large than a LAN, which is mostly limited to a single building or site. Depending upon the type of configuration, this type of network allows you to cover an area from several miles to tens of miles.
A modem (modulator-demodulator) is a device that modulates an analog signal to digital information. It also decodes carrier signals to demodulates the transmitted information.
The main aim of the Modem is to produce a signal that can be transmitted easily and decoded to reproduce the digital data in its original form. Modems are also used for transmitting analog signals, from Light Emitting Diodes (LED) to radio.

Here, are pros/advantage of Modem:
More useful in connecting LAN with the Internet
Speed depends on the cost
The Modem is the most widely used data communication roadway.
ALL ACTIVATER MS OFFICE ,ms office 2016,2013,2019 ,2021
link https://drive.google.com/file/d/16hcVEHtaR8UnJjgqVu3bplW0CSpqHq_K/view?usp=share_link
The QBot malware operation has started to abuse a DLL hijacking flaw in the Windows 10 WordPad program to infect computers, using the legitimate program to evade detection by security software.
A DLL is a library file containing functions that can be used by more than one program at the same time. When an application is launched, it will attempt to load any required DLLs.
It does this by searching through specific Windows folders for the DLL and, when found, loads it. However, Windows applications will prioritize DLLs in the same folder as the executable, loading them before all others.
DLL hijacking is when a threat actor creates a malicious DLL of the same name as a legitimate one, and places it in the early Windows search path, usually the same folder as the executable. When that executable is launched, it will load the malware DLL rather than the legitimate one and execute any malicious commands within it.
QBot abuses WordPad DLL hijacking flaw
QBot, also known as Qakbot, is a Windows malware that initially started as a banking trojan but evolved into a malware dropper. Ransomware gangs, including Black Basta, Egregor, and Prolock, have partnered with the malware operation to gain initial access to corporate networks to conduct extortion attacks.
Security researcher and Cryptolaemus member ProxyLife told BleepingComputer that a new QBot phishing campaign began abusing a DLL hijacking vulnerability in the Windows 10 WordPad executable, write.exe.
While BleepingComputer has not seen the original phishing emails, ProxyLife told us they contain a link to download a file.
When a person clicks on the link it will download a random named ZIP archive from a remote host will be downloaded.
This ZIP file contains two files: document.exe (the Windows 10 WordPad executable) and a DLL file named edputil.dll (used for the DLL hijack).
Contents of the downloaded ZIP fileAs you can see from the properties of the document.exe file, it is simply a renamed copy of the legitimate Write.exe executable used to launch the Windows 10 WordPad document editor.
When document.exe is launched, it automatically attempts to load a legitimate DLL file called edputil.dll, which is normally located in the C:\Windows\System32 folder.
However, when the executable attempts to load edputil.dll, it does not check for it in a specific folder and will load any DLL of the same name found in the same folder as the document.exe executable.
This allows the threat actors to perform DLL hijacking by creating a malicious version of the edputil.dll DLL and storing it in the same folder as document.exe so it is loaded instead.
Once the DLL is loaded, ProxyLife told BleepingComputer that the malware uses C:\Windows\system32\curl.exe to download a DLL camouflaged as a PNG file from a remote host.
This PNG file (actually a DLL) is then executed using rundll32.exe with the following command:
rundll32 c:\users\public\default.png,print
QBot will now quietly run in the background, stealing emails for use in further phishing attacks and eventually downloading other payloads, such as Cobalt Strike (a post-exploitation toolkit threat actors use to gain initial access to the infected device).
This device will then be used as a foothold to spread laterally throughout the network, commonly leading to corporate data theft and ransomware attacks.
By installing QBot through a trusted program like the Windows 10 WordPad (write.exe), the threat actors hope security software will not flag the malware as malicious.
However, using curl.exe means that this infection method will only work on Windows 10 and later, as earlier operating system versions do not include the Curl program.
For the most part, this should not be an issue, as older versions of Windows have been phased out after reaching the end of support.
At this time, the QBot operation has moved on to other infection methods in recent weeks, but it is not uncommon for them to switch to previous tactics in later campaigns.
1:- first off all go to control panel click program and features click uninstall click to view .
c:/ systeminfo.exe
system information and all details update .
at host fix all updated windows security .
cmd open
Finally give the following command to remove the desired update. (e.g. the KB "4058702")
Force Restart
wusa /uninstall /kb:999999 /quiet /forcestart1. Open Command Prompt as Administrator.
2. First, view a list with the installed updates with the DISM command:
* e.g. To remove the "Package_for_KB4058702~31bf3856ad364e35~amd64~~16299.188.1.0"
Tip: If you want to view more details for an installed package then give this command:
e.g: dism /online /get-packageinfo /packagename:Package_for_KB4058702~31bf3856ad364e35~amd64~~16299.188.1.0
4. Finally, type the following command to remove the desired update package and press Enter: *
* e.g. To remove the "Package_for_KB4058702~31bf3856ad364e35~amd64~~16299.188.1.0", give this command:
Tip: To easy type the above command:
1. Copy and Paste the first part (with the bold characters), of the above DISM command, in command prompt window.
2. Then highlight the full package name from the list of installed packages (above) and press the Ctrl + C keys (to copy the full package name on the clipboard).
3. Finally press the Ctrl + V keys (to paste the full package name on the DISM command.)
That’s all folks! Did it work for you?
Please leave a comment in the comment section below or even better: like and share this blog post in the social networks to help spread the word about this solution..